SECURITYBRIDGE BROADENS U.S. REACH WITH NEW 1st BASIS GROUP PARTNERSHIP
Press Release
Ingolstadt, Germany, February 22, 2022 – SAP security provider SecurityBridge—now operating in the U.S.,—today announced a partnership with Wisconsin-based 1st Basis SAP Services Group, (1st Basis). The partnership enables 1st Basis to provide SecurityBridge’s integrated SAP Security platform and services—the most advanced cybersecurity to SAP managed services, and S4HANA migration projects—to their customer base.
“It’s no secret that SAP often holds an organization’s crown jewels and needs to be given the utmost protection. However, according to the latest research 43% of data breaches are at the application layer and we are finding that this is the greatest area of weakness,” said Doug Pastrich, CEO of 1st Basis.
SecurityBridge provides the most advanced cyber-platform with real-time threat detection, vulnerability management, custom code scanning, and patch-management in a seamless one-stop-shop solution, built on a single technology layer. With real-time dashboards based on SAP Fiori, SecurityBridge provides actionable intelligence that can be relied upon to make critical security decisions.
“SecurityBridge provides the most comprehensive functionality and seamlessly integrates within the SAP technology stack. Its agile and holistic approach enables us to provide transformation and managed services very quickly and smoothly. 1st Basis will be building on our solid reputation of providing our clients with the utmost quality of managed services as security is becoming more urgent. With this partnership, we will provide significant speed to security in our ability to reduce the attack surface for our customers by utilizing the power of SecurityBridge,” added Pastrich.
“Threats against SAP systems are becoming more prevalent and more sophisticated. The most effective, proven approach is to combine constant real-time threat monitoring and vulnerability management into a holistic security process’’, said Christoph Nagy, CEO of SecurityBridge.
“The partnership with 1st Basis will be highly synergistic for both parties, as we see the increasing migration towards managed services for SAP clients. We value the expertise and excellent reputation that 1st Basis provides, and we look forward to an exciting year ahead.”
About Security Bridge

SecurityBridge is an SAP Security Platform provider, developing tools to extend the SAP ecosystem. The company takes a radically different approach to traditional security tools, believing SAP applications and custom code will be infiltrated no matter how diligently security hygiene is applied. In response to this belief, SecurityBridge created the world’s only natively integrated real-time solution for constant monitoring. Powered by anomaly detection, the SecurityBridge platform can differentiate between accurate results and false positives so that security teams can better focus on real issues. For more information, please visit securitybridge.com.
About 1st Basis

Founded in 2006, 1st Basis provides affordable, high-quality SAP Basis managed services at SAP Best Practices standards. For over a decade, we have kept that promise. We leverage our unmatched expertise to keep our customers’ SAP systems secure, stable and highly available. For more information, please visit www.1stbasis.com.
Security Concerns with Zoom and SAP
This is a companion piece to our other post on TikTok and potential security concerns with SAP. The geopolitical background issues are the same. China has a history of corporate and other espionage and a history of inserting its interests into the affairs of corporate entities, even technically private ones, at home. It is also the world’s most developed surveillance state, and recently, it and the United States have been increasingly at odds on a variety of issues.
Unlike TikTok, Zoom is not headquartered in China. Its owner, Eric Yuan is originally from China, but moved to the United States in 1997.
The Rise of Zoom
As most people now know, Zoom has been one of the greatest beneficiaries of CoVid lockdowns, seeing an almost twentyfold rise in usage over the past year. People isolating to slow the spread of ‘the virus’ have flocked to the platform for social and work purposes. The subsequent discovery by many workers (and some businesses) that much of what they do doesn’t depend on their being on-site has contributed to its continued expansion. Lots of educational institutions and social services and primary medical services have adapted to employ video as well.
The ease with which Zoom can be accessed and its full but intuitive feature set have spurred its widespread adoption, but that same broad suite of functionalities and ease of access have made it a broad target for hackers and other online bad actors.
The Problematic History
There have been a series of security issues with Zoom that are, perhaps, not surprising given the nature of the platform. Early on, many people using the platform were declining to use the password option, which gave an opening to bombers and grifters to bust in to meetings and wreak havoc. In one infamous example, a major university’s graduation, held online because of CoVid, was interrupted with racial invectives. The platform has been used for information scraping, malware injection, password stealing, and just about anything else a hacker might want to do. At one point, Zoom partnered with a Chinese firm to generate cryptographic keys, which threw up warning signs among politicians and security experts. Additionally, Zoom agreed to de-platform several well-known Chinese dissidents at the request of the Chinese Communist Party (CCP).
The list of exploits and possible vulnerabilities is very long, and you can read about them in depth in this excellent compilation at Tom’s Guide. The most problematic thing about Zoom, though, has been its lack of candor at times, for instance claiming to have inaugurated end-to-end encryption when it hadn’t done so. In response to various criticisms, Zoom has taken steps to mitigate its vulnerabilities, but very few of these steps seem, from an outside perspective, to have been taken proactively. A variety of alternatives to Zoom are available. If you share sensitive information on such a platform, you might be better off to look elsewhere until Zoom has established a more robust security track record, and this is probably more likely to be true of businesses that employ SAP services than those that do not. Zoom’s vulnerabilities make it not just problematic in view of the Chinese, but also corporate espionage, sabotage, and sundry black-hat exploits. As with TikTok, your vulnerability profile will depend entirely on the potential value of the information that you share to those who shouldn’t have it.
TikTok Security Concerns and SAP
Geo-Political Background
Recently, the Trump administration has kicked around the possibility of banning the use of TikTok in the United States. This comes against a backdrop of increasing tensions between the United States and China due to China’s emergence as a military and economic rival superpower, and exacerbated by what some in the West view as China’s military and economic expansionism against a backdrop of long-time institutional infiltration, technological and other espionage, and unfair trade practices. Recently, relations have been further strained by internal Chinese crackdowns on civil dissent, reneging on the conditions of its treaty with Great Britain regarding the status of Hong Kong, and what some (though not all) view as blame for not having blown the whistle earlier about CoVid-19, which has had devastating health, social, and economic consequences around the globe.
India, which has recently clashed with China above the disputed Galwan Valley between China and Indian-administered Kashmir, has banned the popular short-form video plus sound application. There have been rumors, though denied, that Australia and the Philippines might also follow suit. Both of those nations have been alarmed by Chinese expansionism in the South China Sea.
Does TikTok Pose a Danger?
Does the application pose a danger? It’s hard to say. Like most such applications, new versions often are filled with security issues that need to be patched, and TikTok does a comparatively decent job of doing so. The company that owns TiKTok, ByteDance, is headquartered in China, but not ‘owned’ by the government per se. ByteDance swears up and down that it would never convey any user information to the Chinese government, but the rights and responsibilities of ‘private’ corporations in China vis-a-vis the government are more . . . negotiable, let us say, there than they are in the West.
At present, there’s no reason to believe that TikTok collects any more information than other ‘free’ social media applications, such as Facebook and Twitter, which monetize metadata from their users to target ads and such, but following revelations of what Cambridge Analytica was able to infer from access to Facebook’s information during the 2016 election, there is some concern about how China might use such information for similar purposes (or worse) such as: wargaming, propaganda/disinformation and election meddling. We have already seen that they take a very aggressive line against their own citizens at home and abroad who use online platforms to criticize the government, and like the Russians they seem to be cultivating their own troll farms.
With Regard to SAP Users . . .
The problem here is that many SAP users are companies whose information is not only valuable to themselves, but potentially also to others. One of the things that TikTok was criticized for was maintaining access to clipboard information. They were criticized, when found not to have fixed the problem. They excused the delay by saying that there was a conflict with the spam filter. Theoretically, a government with access to such information might leverage it either through simple data mining or blackmail. A surveillance state such as China might exploit or introduce backdoor methods of accessing data on devices with the TikTok application, as they are said to have done with Huawei, their 5G cellphone network.
So there is no clear-cut answer on whether to prevent employees from using TikTok on devices that also might be used for work purposes. As a precaution, and partly because of the conflict, India has banned certain Chinese apps (including TikTok). The State Department would like Microsoft or some other US-based company to buy it. They have given a deadline before it is banned. For the moment, we advise caution.
You have the finest enterprise resource planning (ERP) software available in SAP; now you need to know how to optimize its use. The best way forward is to use the Computing Center Management System (CCMS) to monitor, control, and configure your SAP system.
Monitoring
Your CCMS can conduct system-wide monitoring and automatic reporting. It produces alerts that are assigned a severity and color coded. One of the best attributes of the CCMS monitoring architecture is that it offers a flexible framework so that your specific business landscape can be monitored in the way best suited for you. Instead of one over-arching monitoring and administration program, elements of the monitoring architecture function largely independently of each other.
The CCMS alert monitor includes:
*Status indicators (green, yellow, red) for all components
*Alerts if a status indicator is not in the green range
*Easy access to methods for analyzing alerts
*Alert tracking and management
*Complete, detailed monitoring of the SAP system, host systems, and databases
It is important to note that the release of the 4.0 alert monitor has replaced the previous monitoring and alert system in the CCMS. This new monitor offers all of the functions that were available in the old alert monitor as well as new, more reliable alerts and more advanced and powerful features. CCMS is a feature of Solution Manager and while the capability, along with the software, is free, setup and maintenance is not and can be fairly pricy. Small- to Mid-sized SAP customers may fair better using a 3rd-party solution (like 1st Watch).
Controlling
Optimizing Log on Behaviors. Your CCMS can control how the whole system is being used and automatically improve efficiency by logon load balancing. Load distribution allows you to dynamically distribute SAP users across workprocesses. If you have specified work groups, you can increase their efficiency by setting up multiple logon workgroups. You can assign one or more application servers to certain workgroups or specific applications. When users log on to the system, they are automatically logged on to the server that currently has the best performance statistics or the fewest users. You can assign particularly important workgroups with time-sensitive transactions to application servers with better response times.
Background Processing.
Your CCMS can control the background processing of routine tasks, resource-intensive programs, or long-running programs. With the SAP system, you can choose from a variety of methods for scheduling and managing jobs. You can run both SAP-internal and external programs. And you can run related programs as “job steps” within a single background processing job. That way, a single background job can accomplish a complex task that consists of multiple processing steps.
Configuring
With your CCMS running, SAP Basis administrators can direct the configuration of SAP profiles. SAP profiles are operating system files that contain instance configuration information. Individual configuration parameters can be customized to the requirements of each instance. That means that the professionals at 1st Basis can use configuration parameters to delineate the runtime of elements like main memory size, or shared memory. Your CCMS can determine which work processes the instance itself provides and where other services like database hosts can be found. SAP materials advise that you use the CCMS to maintain configuration profiles. This means that you should not edit the active profiles directly at operating system level.
The CCMS really makes SAP Basis work best for your business. If you have questions or want to make sure that you’re getting the best possible performance of your SAP System, consult with the professionals at 1st Basis. We will assess how your CCMS is functioning and make any adjustments necessary.
“Certain areas of your SAP landscape need to be monitoredon a regular basis to ensure reliable operation.” —SAP Administration: Practical Guide, p. 269 Galileo Press, 2011.
Monitoring is an essential part of the daily tasks of any SAP Basis Administrator. In the past, this was accomplished by logging into certain transactions once or twice a day and looking at specific parameters. As one who did this for several years, I can tell you that humans are the worst kind of resource to leverage for this. We are subject to change blindness and are easily bored by mindless repetitive tasks. Monitoring should be done exclusively by computers.
Managed Service Provider (MSP):A monitoring system on its own is just an alert generator and not much use without someone to alert to. If an alert happens and no one notices; does it make a difference? This is where many companies go awry, they set up a monitoring system, but don’t think about who will answer the alerts. Often, the internal Basis team is the wrong answer. They are too busy and, frankly, too expensive to be tasked with this. Help desk technicians are sometimes chosen for this, but they don’t know a critical SAP issue from a non-critical one—or how to fix it. Typically, they wake up or forward the issue to the Basis team. An MSP, like 1st Basismonitoring the SAP landscape remotely, is the best option for small-to-medium sized enterprises.
Every Basis support agreement 1st Basis issues includes Monitoring with our automated solution. Our system uses a .Netconnector and SAProuter(both standard methods for connecting to SAP). If a Sensory Nodeis required inside our customer’s network, it connects with our NOC Admin Node over a single TLS tunnel.
It took 3 years to build our monitoring solution after some dead ends (Nagios). Over the years we have learned what works and what doesn’t when it comes to best-practices. The main lesson was that simplicity has its own utility and reduces overhead and TCO.
Here is a smattering of the other lessons we’ve learned along the way:
- Standard SAP Connections are best
- .Net and JCo connectors
- SAProuter
- RFCs are OK, but add overhead
- Avoid systems that rely on agents
- Often a point of failure
- They add overhead to update and maintain
- They are difficult to get approval for
- Overly complicate the architecture
- Alerts are not the goal
- Too many alerts obscure actionable items
- Too much REDteaches
responders that “critical” is normal - Systems with Parent/Child validation reduce alert
noise
For companies that do not want to hire an MSP or Basis group to do their monitoring, there are a number of solutions available. These are some of the solutions we have investigated as possible replacements for our system. Buying off the shelf is a better solution than DIY.
Solution Manager 7.2:SAP has made some big improvements with 7.2 with regard to monitoring, but this is still a large-company solution and a little too DIY. While advocates claim it is “free” the cost of implementing, configuring and maintaining the solution is not and their ROI estimates are dubious. Handling the alerts requires a team of SAP Basis administrators. But, for large companies like Rockwell Automation or Bemis, a 2- to 3-year implementation and dedicated team may make sense. They report the biggest time investment is in setting up roles and security objects and getting agents configured on all systems to be monitored.
sysink Xandria:Has been in the business of providing a viable monitoring solution for about a decade. Their solution is mature and well thought out and you can tell that it was designed by Basis administrators; for Basis administrators. The company was founded in Switzerland and has only recently targeted the United States, so they are big in Europe, but somewhat new to American businesses. The founders are former Basis administrators who designed a monitoring solution of their own as well. They have enlisted another former Basis administrator with a background in monitoring system implementation as Director of Sales Engineering, Tyler Constable. He knows the product well and how to sell it to Basis administrators and MSPs. The system has two drawbacks which they assure us are correctable: it uses some agents and the UI is reminiscent of RZ20, which is not surprising given the developers are all Basis admins as well. (see my Blog on UX Matters). Here is a small sample of the UI:
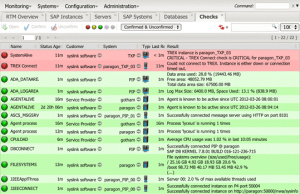
These are the pros and cons for Xandria:
- Pros:
- Geared toward Basis Admins and MSPs
- Global edits to threshold templates
- Uses alert conditional logic (if/then, and/or)
- Cons:
- Uses agents, but has agent-less options
- User Interface is dated and kludgy
Foglogic:Is new to the SAP monitoring scene and is still in Beta, but they are definitely one to watch. Their UI is modern, clean and colorful and they have a strong grasp of data analytics. The solution is less tailored to SAP Basis monitoring than Xandria, but they have a lot of things right. The company was founded by Ashock Santhanamand Chandy Nilakantan, former CEOs and CTOs respectively. Together, they make a strong team and are a pleasure to deal with. Chandy’s enthusiasm for analytics is infectious. They are proud of their solution and they should be.
These are the pros and cons for Foglogic:
- Pros:
- Modern User Interface
- Strong analytics with multiple views
- Uses JCo Connector
- Cons:
- Still in Beta
- Monitoring is not real-time
- Multiple modes of data transfer instead of JSON
- Multiple connection methods including POST
The dirty little secret for Basis teams (internal and external) is that monitoring is often given a back seat to putting out fires. This becomes a vicious cycle as monitoring is meant to prevent fires. For most companies, outsourcing monitoring and remediation to an MSP (domestically) is a more economical solution. Especially for systems that require High Availability (HA) around the clock. In any case, these monitoring tools are a boon to the Basis team and by extension to the enterprise in an often neglected area. SAP calls monitoring “Critical Tasks Checks”. Our experience confirms; daily monitoring the SAP landscape is Critical.
—David Beiswenger.




