Password complexity changes as recommended by NIST![]()
What does your password say about you? If it says “password” or is simply a string of letters, numbers and symbols, then you might want to consider changing it. Passwords are important for personal security, but not all of them are of equal quality. It turns out that what makes for a good password is a complex question of probability and human factors. This question was put to a mid-level manager, Bill Burr, at the National Institute of Standards and Technology (NIST) back in 2003.
1
The password advice from NIST became influential not just within the federal government but on corporate networks, websites and mobile devices as well.
NIST SP 800-63B Special Publication – 2003
The initial recommendation included these simple rules:
- lowercase letters
- uppercase letters
- numbers
- special characters (@, !, $, etc.)
- changed regularly

That last rule became an issue for IT departments and led to weaker passwords as people would make minor modifications that were easy to guess. Which is more secure? “password123” or “P@ssW0rd123!”? The latter follows the NIST rules above but is actually not an improvement. The requirement to change passwords regularly lead people to add memorable characters like 1, 2, 3 as iterations which were predictable and not more secure. This requirement and others often led to passwords being scribbled on Post-It notes adhered to the computer screen as they were beyond the recollection capabilities of most users. Humans naturally began substituting numbers for similarly shaped letters or vowels (as in our password transformation example above). They also used easily remembered numbers like birthdays and words like, “friends” or a sequence of numbers like, “12345”—the famed password of planet Druidia’s defense shield in Space Balls the Movie. 2
NIST SP 800-63B Special Publication – 2017![]()
This NIST SP offers stronger password requirements than the NIST Password Guidance published in 2003. NIST’s Special Publication 800-63B provides federal agencies with more stringent password requirements for authentication of federal systems and identities. NIST SP 800-63B includes technical changes and clarifications to NIST SP 800-63A. NIST Special Publication 800-63B3
requires the use of at least three character types from at least two of the following four categories:
- lowercase letters
- uppercase letters
- numbers
- special characters (@, !, $, etc.)
In addition, NIST Special Publication 800-63B mandates a minimum length of eight characters. The number of special characters required has also been increased from one to two. These updates are important because they make it more difficult for hackers to guess passwords. NIST’s Special Publication 800-63B also requires that passwords be at least 8 characters in length. Increasing the number of special characters required and mandating a minimum length make it more difficult for hackers to crack passwords through brute force attacks.
Link for The Wall Street Journal Here
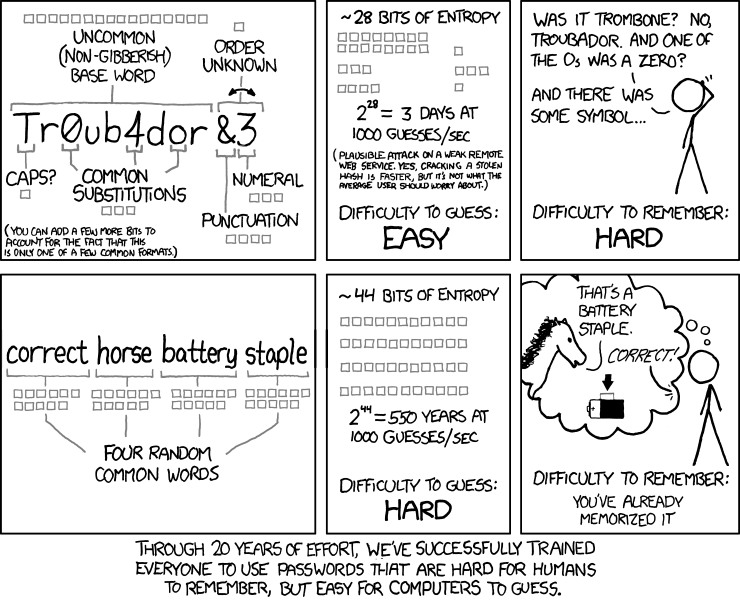
“In a widely circulated piece, cartoonist Randall Munroe calculated it would take 550 years to crack the password “correct horse battery staple,” all written as one word. The password Tr0ub4dor&3—a typical example of a password using Mr. Burr’s old rules—could be cracked in three days, according to Mr. Munroe’s calculations, which have been verified by computer-science specialists.”
NIST’s goal with these updates is to improve the security of federal systems while also making it easier for users to remember their passwords. NIST’s updated requirements make it possible for users to create longer and more complex passwords that are still easy to remember. This update reflects the evolution of technology and accounts for the impact that new types of information, such as biometrics or tokens, can have on authentication processes. Passwords are essential for protecting your online identity.
NIST SP 800-63B-3 Special Publication – 2020
NIST Special Publication 800-63B- update was publish in March 2020 with new information on identity proofing and authentication. This revised publication provides guidance to organizations on how to strengthen the security of digital identities. It is important for IT managers to understand the changes in this publication so they can ensure their organization’s digital identities are secure. The new guidelines are informed by better data on password breaches and contain some interesting updates.
The new NIST guidelines that you include these elements in your new password policy:
Password Authentication
- Enable “Show Password While Typing”
- Allow Password “Paste-In”
- Use Breached Password Protection
- Don’t Use “Password Hints”
- Limit Password Attempts
- Use Multi-Factor Authentication (MFA)
- SMS may not meet OOB
(out-of-band authenticators)
requirements
- SMS may not meet OOB
Password Creation
- Greater Length over Complexity
- No more periodic resets
Password Storage
- Secure Databases
- Hash Users’ Passwords
These core guidelines are worth looking at in more detail.
Password Creation
While password complexity is important, it is also crucial to have a password that is long enough to be secure. NIST SP 800-63B-3 recommends at least 8 characters for passwords. Increasing the length of your password increases the complexity and makes it more difficult for hackers to guess. While passwords that are at least 8 characters long can be found by hackers, they are not as commonly used. It is important to note that the creation of separate, unique passwords for each application does not eliminate the need for strong passwords—it simply makes them easier to manage. Although attackers do not have access to all applications at once, an individual account can provide them with direct access to sensitive information such as credit card numbers and social security numbers by its reuse across multiple applications. Randomly generated passwords can be used as a starting point for creating your own personalized, long and complex password. The length will ensure that it is not easily guessed, but the randomness means that it cannot be recalled by a human being either. There are several different implementations of random password generators, some simple and some complex, but all of which provide benefits over the use of standard passwords. The end of mandatory resets was one of the top 3 issues when a draft came out in 2012 (the other two were similar problems with multi-factor authentication). To cope with the fact that passwords are inherently breakable, users were forced to carry out periodic resets (most people do it every 90 days), generating new passwords and distributing them to all systems requiring authentication. This has many failings:
- Password reset mechanisms are inherently insecure; everyone knows how easy they are to bypass, even when there is no reason to be suspicious of the user.
- Password reset mechanisms inflict excess load on IT support staff, who must distribute and then destroy these password reset tokens.
- Password reset mechanisms do not help with security at all; they just shift the burden onto users.
Password Authentication
Typos are a common occurrence in the world of passwords. There is no better way to decrease your error rates than having users see what they did wrong when trying to log-in except by showing them exactly where their typing went wrong with the “show password” option enabled. The paste-in function of the password manager will require people to create longer passwords, but in turn it makes them more compliant and safe. Many are using a tool like LastPass which automatically generates complex passwords for every site they visit. Users only have to remember the tool’s master password and then they have access to all of their passwords. New passwords should be checked against a “blacklist” of compromised passwords. This helps keep your account secure by not allowing anyone who might have the original data (i.e., hackers) access to steal things like usernames and personal details with their corresponding user names/passwords. This is called Breached Password Protection (BPP). The password complexity requirements lead to more help with remembering the password in the form of password hints. Password hints are a way to use clues about the password as prompts for users so they can remember it. The new NIST SP 800-63B-3 Special Publication requires that any hint given be disabled, and notes that including a “hint” is a practice that should not be employed anymore. One of the main concerns for the guidelines is the number of times a password can be attempted before they are locked out. The new NIST SP 800-63B-3 Special Publication recommends a limit of three attempts. After three failed attempts, the user would then be required to wait for a period of time before attempting again. This measure is meant to protect accounts from being hacked or compromised. Multi-factor authentication is an extra layer of security that is used in addition to passwords. It requires the use of more than one type of authentication credential. The basic concepts include these multiple factors working together:
- “something you know” (like a password)
- “something you have” (like a phone)
- “something you are” (like a fingerprint)
SMS-based multi-factor authentication has been a convenient way to provide this extra layer of security. However, there have been concerns about its security. One of the main concerns about SMS-based multi-factor authentication is that the text messages can be intercepted. This means that someone who is not authorized to access the account could potentially receive the text message with the verification code and be able to log into the account.

Password Storage
To protect your users’ passwords, it is important that only essential personnel have access to the database. In addition, after a user’s password is changed by an administrator or automated system, access to the hash of the user’s old password should be removed from all system components. If the user’s password was updated because of a security compromise (e.g. a data breach), this best practice becomes even more important. Follow NIST guidelines for admin passwords also.
Passwords should be hashed with interim storage. In this case, a hash function is used on a password and stored in an encoded form. A Salt is used to make it more difficult for an attacker gain access to hashes through a brute-force attack. A salt is a fixed-length string of characters that is usually stored separately from the encrypted password. The string is appended to the password before being hashed and then combined with the resulting hash. Salts are created from random data, which reduces the risk of big data breaches if one occurs.
Bad Passwords a-Dressed
I’ve had people look at it and they’re like, ‘Oh, I’d better go change my passwords,’
It turns out after lots of data analysis, we think we are being clever about how we construct our passwords designed to foil hackers but the results of the data show we are not. In 2003, Mr. Burr didn’t have the data to understand this. Today it is obvious to people like Lorrie Faith Cranor who has spent years studying terrible concoctions and putting 500 of the most common passwords on a blue shift dress.[7] The garment had been infused with the most common passcodes–“princess,” “monkey,” “iloveyou” etc.—a few that are unprintable here. At the 2015 during Stanford’s White House cybersecurity summit the dress prompted careful study from those around her as well as some embarrassment.[8]
Conclusion![]()
NIST SP 800-63B-3, provides guidance for managing digital identity in a world that is increasingly reliant on technology to work and communicate with others. There are many changes from previous editions yet many similarities as well. These standards should be followed by all organizations who store sensitive personal data or provide online services where people can create an account and log into their accounts using passwords. If you’re not sure how best to comply with these guidelines or need help understanding what they mean for your organization’s authentication process, contact 1st Basis today.





